In this part, we are going to introduce this tutorial and companies involved in this tutorial.
This will be based on what i’ve done at KeeeX, the SME i’m employed in.
About this tutorial
What are we talking about?
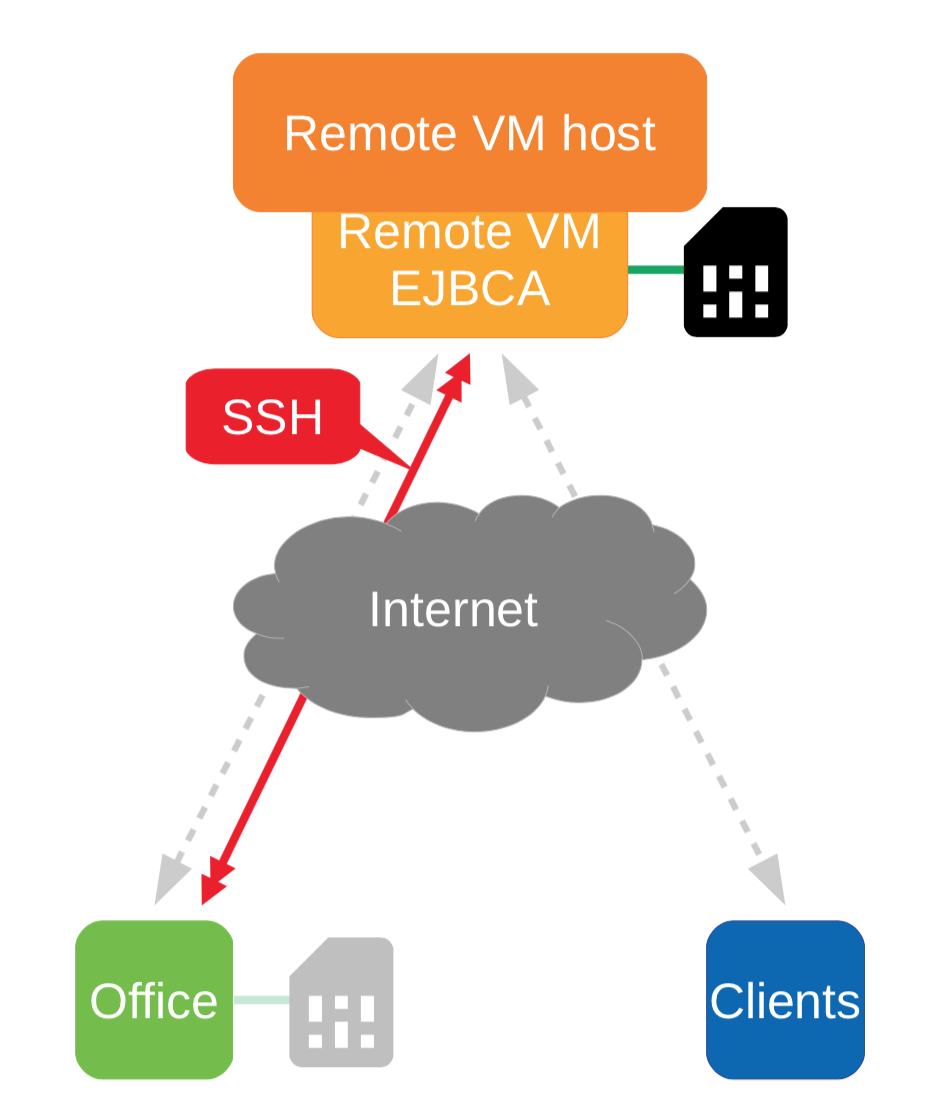
The goal of this tutorial is to build a relatively secure and cheap PKI for your business, organization or personal use, by :
- Installing and basically securing a full PKI software, EJBCA, on a Debian Stretch VM,
- Securely forwarding a HSM through the Internet from your office to the VM for EJBCA use through SSH
AMUSec Conference slideshow (in French)
You can get French AMUSec conference slideshow here : Slides in French
An English-translated version can be made on demand if asked 😉
Companies involved

KeeeX
What is KeeeX?
The KeeeX company was founded in December 2014 by Laurent Henocque, an engineer from Ecole Polytechnique (X82), lecturer researcher at Aix Marseille University, CNRS, with a focus on constraint programming, and semantic web expertise.
KeeeX was an answer to a number of questions:
- how to warrant the authenticity of digital information independently of any web service, dedicated infrastructure?
- how to preserve the oganisation and links between files across multiple storage locations?
- how to find files instantly whichever their location on the internet or a disk?
What is KeeeX doing?
KeeeX injects trusted metadata into your files without changing the format and readability of your documents and data. They are timestamped in real time and their unique hash is anchored by default on the Bitcoin Blockchain to prove the existence of the file on a given date.
By sealing proofs of integrity and authenticity in your documents, you can be sure that the document (+250 file formats supported) is an unmodified original and that you are the author of it. KeeeX also adds tags to facilitate search and allows cryptographic linking between files (versioning, appendix …).
What are you doing there?
I’m a IT engineer with many roles: multi-tasking developer (mobile apps, some backends and services), sysadmin and Data Protection Officer (in accordance to GDPR).
Edit: No longer working there since 1st of April 2019. Working as an independant now.
To cryptographers/infosec comrades: Did you wrote “blockchain”?
We are using Bitcoin Blockchain for time proofs. Only for time proofs. And it works fine.
And anyway if you don’t believe, we’re using standard RFC3161 Timestamping (and this is one of the reasons we need a PKI).
Why do you need a PKI?
As a part-time sysadmin at KeeeX, it was clear to me that we needed to use a PKI for many reasons:
- to have a Trusted Timestamping infrastructure with reliable X509 certificates and in accordance to RFC3161;
- to ensure employees identities when authenticating through our Virtual Private Networks;
- to protect KeeeX internal services and infrastructure with TLS certificates, and TLS client authentication.
EJBCA
What is EJBCA?
EJBCA® is a PKI Certificate Authority software, built using Java (JEE) technology. There are two versions: the Community one, licensed LGPL; and the Enterprise one, with more features and support.
What is the license of this software?
This software is licensed as LGPL.
Why EJBCA? Why not <insert name here>? Are you working at EJBCA/PrimeKey?
EJBCA because it was advised by a friend of mine (hello Frédéric 🙂 ), i don’t have the same knowledge in <insert name here>, and i’m not at all working for PrimeKey.
Where can i find EJBCA support for Community Edition?
Their official support forum is here: https://sourceforge.net/p/ejbca/discussion/
These people are very nice, and answer within few days, which is great.
Hello to Tomas and EJBCA team if they read this. 😉
Nitrokey
What is Nitrokey?
Nitrokey is an USB key to enable highly secure encryption and signing of emails and data, as well as login to the Web, networks and computers. Their Nitrokey HSM product is very interesting: Nitrokey HSM secures cryptographic keys of your own PKI and your server.
What can I do with this?
Nitrokey HSM features:
- Up to 31 ECC GF(p) 256-bit keys storage,
- Up to 20 RSA 2048-bit keys storage,
- Based on SmartCard-HSM,
- Both hardware and software are open-source and free software. All development tools are available as open source and for free.
- Your secret keys are stored in the tamper-resistant and PIN-protected device and are secured against computer viruses, loss and theft.
- The device is PIN-protected and is secured against hardware attacks.
- Backups protect against loss.
- It’s 60€. Yes.
We’re gonna use it to store critical private keys with EJBCA. You can get a detailed fact sheet here.
Are you working at Nitrokey?
I’m not at all working for Nitrokey.




Nicely written
Cheers,
Mike (who works at PrimeKey =))
Hi Mike,
Thanks, greatly appreciated!
Max
Update: The new Nitrokey HSM 2 supports up to 300 keys, RSA-4096 and ECC-512. See: https://www.nitrokey.com/files/doc/Nitrokey_HSM_factsheet.pdf
Hi Jan, this means I need to make a new purchase, and retest my tutorial with the new Nitrokey HSM 2!
Glad to see RSA 4096 bits in the new version! 🙂
Also very happy to see Nitrokey team (if you indeed are) comming around my blog <3
Have a nice evening
You are my hero, you know that? Thank you so much for this. You saved us all